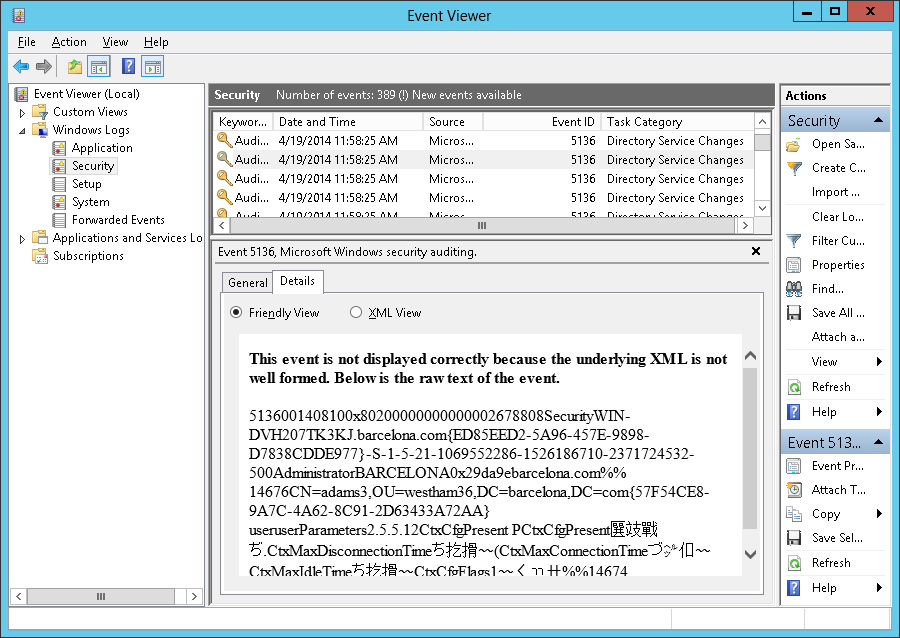
UserParameters attribute of a user object in Active Directory messing up the event detail in Event Viewer in Windows Server 2012.
In Active Directory, userParameters attribute of a user object is used to store the terminal profile setting for a user. Turns out that the userparameters attribute stores the terminal profile data in binary format. Yesterday, I was working on an application where there was a requirement to read the Windows Event log to get the audit data for changes in Active Directory. So I open the Windows Server 2012 Event Viewer to see the log for Active Directory User updates. In Event Viewer screen, following error message is showing in details view of event Meta data. Reason for this error is that event viewer is unable to parse the userParameters blob data. But this problem is only happening with Windows Server 2012 not with Windows Server 2008.