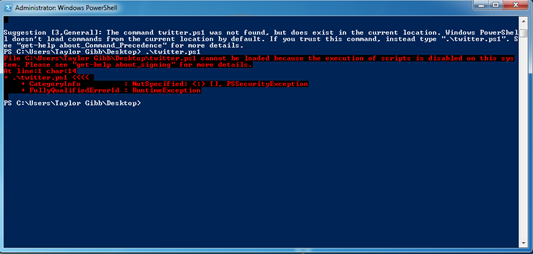
If you have not previously configured PowerShell and try to run it, it may throw a nasty error in red font to scare you, but there is an easy fix for it.
- PowerShell Script Error
PowerShell has a number of execution modes that define what type of code it is permitted to run, this is governed by a registry key that lives in the HKLM hive. There are 4 different execution modes, they are:
Restricted: Default execution policy, does not run scripts, interactive commands only.
All Signed: Runs scripts; all scripts and configuration files must be signed by a publisher that you trust; opens you to the risk of running signed (but malicious) scripts, after confirming that you trust the publisher.
Remote Signed: Local scripts run without signature. Any downloaded scripts need a digital signature, even a UNC path.
Unrestricted:Runs scripts; all scripts and configuration files downloaded from communication applications such as Microsoft Outlook, Internet Explorer, Outlook Express and Windows Messenger run after confirming that you understand the file originated from the Internet; no digital signature is required; opens you to the risk of running unsigned, malicious scripts downloaded from these applications
Restricted: Default execution policy, does not run scripts, interactive commands only.All Signed: Runs scripts; all scripts and configuration files must be signed by a publisher that you trust; opens you to the risk of running signed (but malicious) scripts, after confirming that you trust the publisher.Remote Signed: Local scripts run without signature. Any downloaded scripts need a digital signature, even a UNC path.Unrestricted:Runs scripts; all scripts and configuration files downloaded from communication applications such as Microsoft Outlook, Internet Explorer, Outlook Express and Windows Messenger run after confirming that you understand the file originated from the Internet; no digital signature is required; opens you to the risk of running unsigned, malicious scripts downloaded from these applications
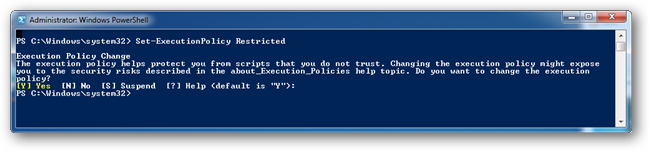
The default execution policy of PowerShell is called Restricted. In this mode, PowerShell operates as an interactive shell only. It does not run scripts, and loads only configuration files signed by a publisher that you trust. If you are getting the nasty red error the most probable cause is that you are trying to run an unsigned script. The safest thing to do is to change the Execution Policy to unrestricted, run your script and then change it back to restricted.
To change it to unrestricted run the following command from an administrative PowerShell:
Set-ExecutionPolicy Unrestricted
You will be asked if you are sure that you want to change the Execution Policy hit the enter button again.
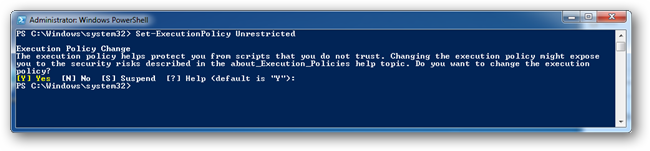 You can now run your downloaded scripts without a problem. However, it’s a serious security risk if you forget to set the Execution Policy back to Restricted mode. You could probably guess how to set it back to Restricted, but incase you don’t:
You can now run your downloaded scripts without a problem. However, it’s a serious security risk if you forget to set the Execution Policy back to Restricted mode. You could probably guess how to set it back to Restricted, but incase you don’t:
Set-ExecutionPolicy Restricted
Again you will be asked if you are sure that you want to change the execution mode, go ahead and hit enter.